Service Desk Software Technical & Development Features
At the core of IncidentMonitor™ is a robust work flow engine. This work flow engine is used to develop the out-of-box, ITIL®-enabled processes. Our customers have full access to the work flow engine to modify the out-of-box process, or add their own custom processes. We strongly believe that giving our customers the option to adapt IncidentMonitor™ to support their needs today, and well into the future, is a critical feature of the application. Modification of the out-of-box processes or implementation of custom processes DOES NOT impact upgrading to the latest version of IncidentMonitor™. All customizations are upgraded with no additional effort required. Plus, we will upgrade your system (On-Premise or SaaS) at NO COST!
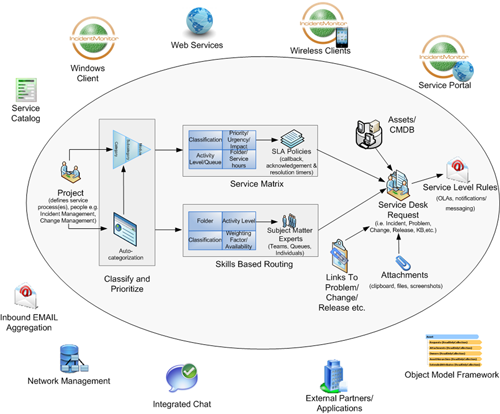
- Single platform to develop, test and maintain significantly reduces Monitor 24-7's cost and supports rapid product development. Our cost savings is passed to our clients in the form of lower license cost.
- Open architecture interacts with other products and platforms using standards based technologies eg COM, XML, .NET.
- Advanced automation for authorizations, approvals, alerts, and dynamic field changes.
- Collaboration between processes (e.g. Incident/Problem, Incident/Change, Problem/Change, etc.) is fully automated.
- Snap-Ins allow you to add your own custom controls on companies, contacts, requests or assets in addition to the menu system.
- Synchronous/Asynchronous scripting can be added to tasks to support before/after events that allow you to add your own custom logic that participates with IncidentMonitor™ transactions.
- Service Rules can use asynchronous scripting for extra flexibility and custom operations.
- Security Controlled Custom Menus allows you to add custom windows using security controlled access.
- XML interchange for communicating with other systems as part of the core transactions.
- Component Object Model (COM) objects can be leveraged in event logic and other applications for tailored, interactive functionality.
- Single Sign On using Active Directory, LDAP, eDirectory and NetWare NDS Support allowing users to be authenticated via other directory systems.
- Dynamic Contact Synchronization to any directory system such as Active Directory, LDAP, eDirectory and NetWare NDS.
- Flexible Role Based Security allows all aspects of the system to be enabled/disabled for security groups.
- Password aging and complexity rules to age out passwords and enforce complexity rules.
- Security Role Delegation allows you to control who can assign other users to security roles.
- Advanced and flexible architecture. Read more why you should select a tool with a well designed architecture. Just imagine buying a house without a solid foundation...









